MimiPenguin – Dump (Hack) Login Passwords of Linux Users
MimiPenguin is a free and open source, simple yet powerful Shell/Python script used to dump the login credentials (usernames and passwords) from the current Linux desktop user and it has been tested on various Linux distributions.
Additionally, it supports applications such as VSFTPd (active FTP client connections), Apache2 (active/old HTTP BASIC AUTH sessions but this requires Gcore), and OpenSSH-server (active SSH connections with sudo command usage).
Importantly, it’s gradually being ported to numerous languages to support all imaginable post-exploit situations.
How Does MimiPenguin Work?
To understand how MimiPenguin works, you need to keep in mind that all if not most Linux distributions store a great deal of such critical information as credentials, encryption keys, as well as personal data in memory.
Particularly usernames and passwords are held by processes (running programs) in memory and stored as plain text for relatively long periods of time.
MimiPenguin technically exploits these clear-text credentials in memory – it dumps a process and extracts lines that have a likelihood of accommodating clear-text credentials.
It then tries to perform a calculation of each word’s chances of being present by determining hashes in /etc/shadow, memory, and regex searches. Once it finds any, it prints them on standard output.
Installing MimiPenguin in Linux Systems
We will use git to clone the MimiPenguin repository, so first install git on the system if in case you don’t have it.
$ sudo apt install git [On Debian, Ubuntu and Mint] $ sudo yum install git [On RHEL/CentOS/Fedora and Rocky/AlmaLinux] $ sudo emerge -a git [On Gentoo Linux] $ sudo apk add git [On Alpine Linux] $ sudo pacman -S git [On Arch Linux] $ sudo zypper install git [On OpenSUSE]
Then clone the MimiPenguin directory in your home folder (anywhere else) as shown.
$ git clone https://github.com/huntergregal/mimipenguin.git
View Linux User Passwords
Once you have downloaded the directory, move into it and run mimipenguin as follows:
$ cd mimipenguin/ $ ./mimipenguin.sh
Note: If you encounter the error below, use the sudo command like so:
Root required - You are dumping memory... Even mimikatz requires an administrator
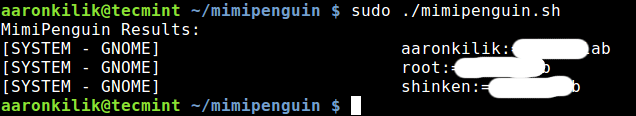
From the output above, mimipenguin provides you with the desktop environment along with the username and password.
Alternatively, run the Python script as follows:
$ sudo ./mimipenguin.py
Note that sometimes gcore may hang the script (this is a known problem with gcore).
Future Updates
Below is a list of features yet to be added to mimipenguin:
- Improving overall effectiveness
- Adding more support and other credential locations
- Including support for non-desktop environments
- Adding support for LDAP
Do share any additional ideas relating to the mimipenguin tool or issues of cleartext credentials in memory in Linux via the comment section below.