How to Install and Configure OpenSSH Server In Linux
Being a network administrator requires deep knowledge of remote login protocols such as rlogin, telnet, and ssh. The one I will discuss in this article is ssh.
SSH is a secure remote protocol that is used to work remotely on other machines or transfer data between computers using SCP (Secure Copy) command. But, what is OpenSSH, and how to install it in your Linux distribution?
What is OpenSSH?
OpenSSH is a free open-source set of computer tools used to provide secure and encrypted communication over a computer network by using the ssh protocol. Many people, new to computers and protocols, create a misconception about OpenSSH, they think it is a protocol, but it is not, it is a set of computer programs that use the ssh protocol.
OpenSSH is developed by the Open BSD group and it is released under a Simplified BSD License. A main factor that has made it possible for OpenSSH to be used so much among system administrators is its multi-platform capability and very useful nice features it has.
The latest version is OpenSSH 9.3 which has been released on 15 March 2023 and comes with many new features and patches, so if you already use OpenSSH for administering your machines, I suggest you do an upgrade or install ssh from the source.
Why Use OpenSSH Over Telnet Or Ftp?
The most important reason why one should use OpenSSH tools over ftp and Telnet is that all communications and user credentials using OpenSSH are encrypted, and they are also protected from man-in-middle attacks. If a third party tries to intercept your connection, OpenSSH detects it and informs you about that.
OpenSSH Features
- Secure Communication
- Strong Encryption (3DES, Blowfish, AES, Arcfour)
- X11 Forwarding (encrypt X Window System traffic)
- Port Forwarding (encrypted channels for legacy protocols)
- Strong Authentication (Public Key, One-Time Password, and Kerberos Authentication)
- Agent Forwarding (Single-Sign-On)
- Interoperability (Compliance with SSH 1.3, 1.5, and 2.0 protocol Standards)
- SFTP client and server support in both SSH1 and SSH2 protocols.
- Kerberos and AFS Ticket Passing
- Data Compression
Install OpenSSH Server on Linux
To install OpenSSH, open a terminal and run the following commands with superuser permissions.
On Debian/Ubuntu/Linux Mint
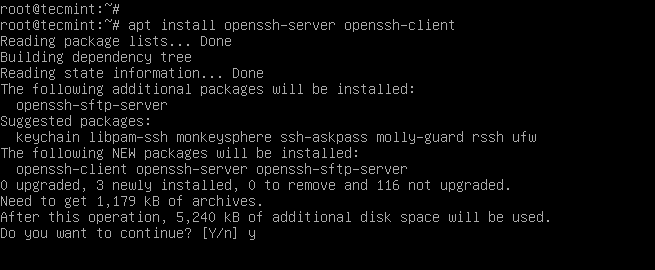
On Debian-based distributions, you can use the following apt command to install the openssh server and client as shown.
$ sudo apt install openssh-server openssh-client
On RHEL/Centos/Fedora
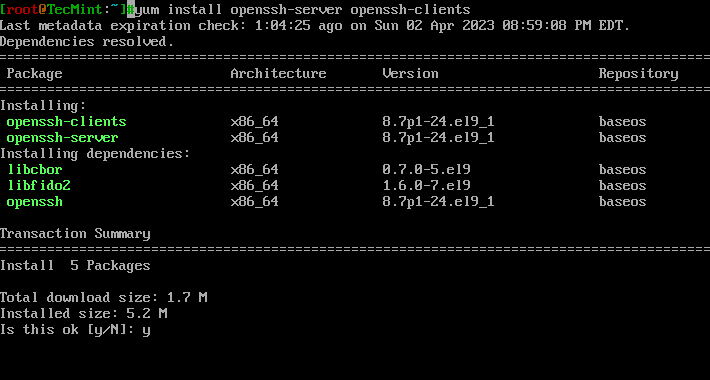
On RedHat-based distribution, type the following yum command to install the openssh server and client.
# yum -y install openssh-server openssh-clients
Configure OpenSSH Server in Linux
It’s time to configure our OpenSSH behavior through the ssh config file, but before editing the /etc/ssh/sshd_config file we need to back up a copy of it, so in case we make any mistake we have the original copy.
Open a terminal and run the following cp command to make a copy of the original sshd configuration file.
$ sudo cp /etc/ssh/sshd_config /etc/ssh/sshd_config.original_copy
As you can see from the command I typed, I added the original_copy suffix, so every time I see this file I know it is an original copy of the sshd config file.
How Do I Connect to OpenSSH
Before we go further, we need to verify if our openssh server is working or not. How to do that? You can try to connect to the openssh server from your localhost through your openssh client or do a portscan with nmap, but I like to use a small tool called netcat, also known as the TCP/IP Swiss army knife. I love working with this amazing tool on my machine, so let me show it to you.
# nc -v -z 127.0.0.1 22
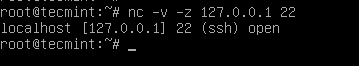
Referring to the netcat results, the ssh service is running on port 22 on my machine. Very good! What if we want to use another port, instead of 22? We can do that by editing the sshd configuration file.
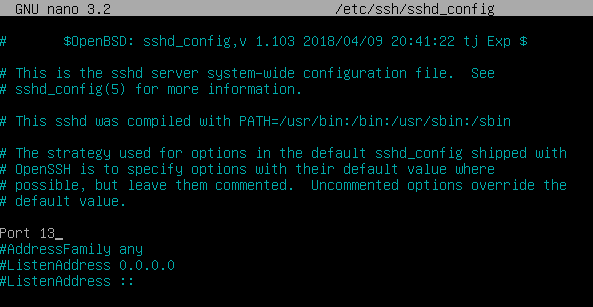
Change SSH Port
Set your OpenSSH to listen on TCP port 13 instead of the default TCP port 22. Open the sshd_config file with your favorite text editor and change the port directive to 13.
Port 13
Restart the OpenSSH server so the changes in the config file can take place by typing the following command and running netcat to verify if the port you set for listening is open or not.
$ sudo systemctl restart sshd
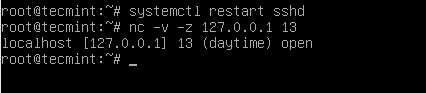
Should we verify if our openssh server is listening on port 13, or not? This verification is necessary, so I am calling my lovely tool netcat to help me do the job.
# nc -v -z 127.0.0.1 13
Do you like to make your openssh server display a nice login banner? You can do it by modifying the content of the /etc/issue.net file.
$ nano /etc/issue.net
Paste the following banner message.
Authorized access only! If you are not authorized to access or use this system, disconnect now!
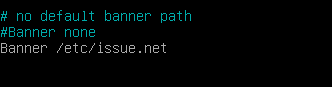
Next, add the following line inside the sshd configuration file.
Banner /etc/issue.net
After making changes to the SSH configuration, make sure to restart.
$ sudo systemctl restart sshd
Conclusion
There are many things you can do with the openssh tools when it comes to the way you configure your openssh server, I can say that your imagination is the limit!