FOSS Weekly #23.29: Linux Mint 21.2 Released, Systemd vs Init, Terminal vs Nautilus and More
Linux Mint 21.2 is available to upgrade now. Also learn a thing or two about systemd in this FOSS Weekly edition.

Linux Mint 21.2 is available to upgrade now. Also learn a thing or two about systemd in this FOSS Weekly edition.
Here are a few tips and tweaks to save your time by combining the terminal and the file manager in Linux.
The post How to Use Man Pages Efficiently in Linux first appeared on Tecmint: Linux Howtos, Tutorials & Guides .
Good documentation is absolutely necessary for any software, and this principle extends to Linux commands as well. Numerous Linux distributions and open-source communities offer comprehensive
The post How to Use Man Pages Efficiently in Linux first appeared on Tecmint: Linux Howtos, Tutorials & Guides.
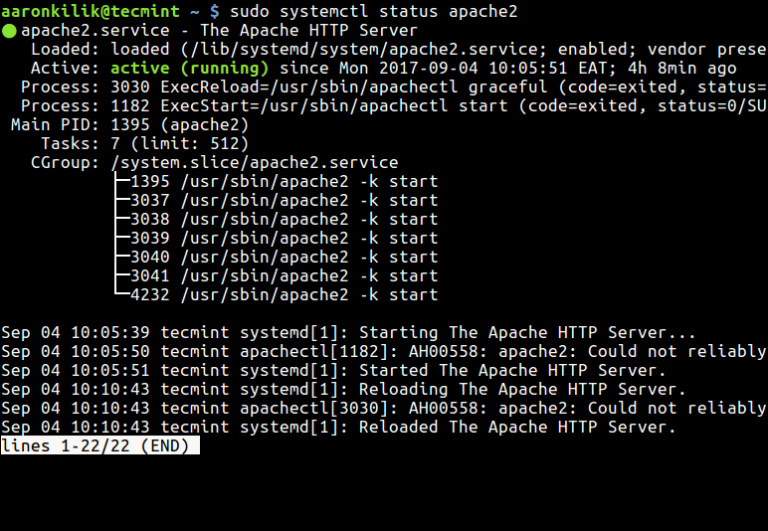
The post 3 Methods to Check Apache Server Status and Uptime in Linux first appeared on Tecmint: Linux Howtos, Tutorials & Guides .
Apache is the world’s most popular, cross-platform HTTP web server that is commonly used in Linux and Unix platforms to deploy and run web applications
The post 3 Methods to Check Apache Server Status and Uptime in Linux first appeared on Tecmint: Linux Howtos, Tutorials & Guides.
The post How to View Colored Man Pages in Linux first appeared on Tecmint: Linux Howtos, Tutorials & Guides .
In Unix-like operating systems, a man page (in full manual page) is a documentation for a terminal-based program/tool/utility (commonly known as a command). It contains
The post How to View Colored Man Pages in Linux first appeared on Tecmint: Linux Howtos, Tutorials & Guides.
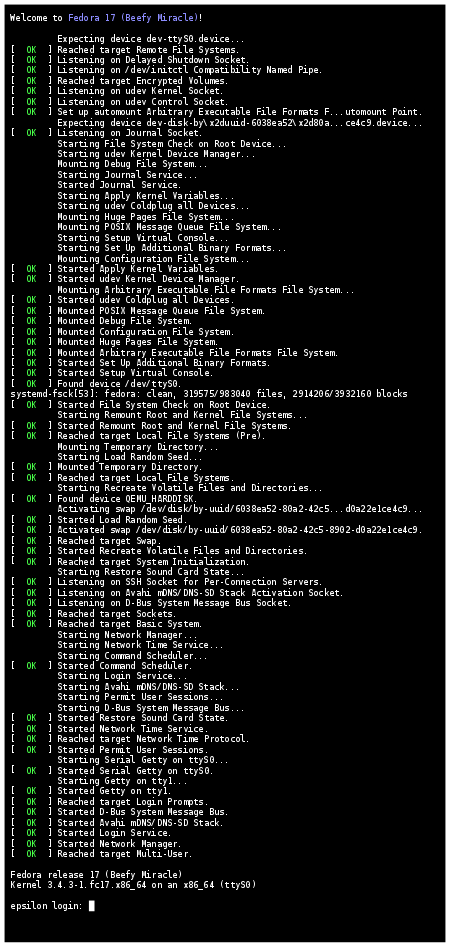
Still confused about what is systemd and why it is often at the center of controversy in the Linux world? I try to answer in simpler words.
The post 35 Practical Examples of Linux Find Command first appeared on Tecmint: Linux Howtos, Tutorials & Guides .
The Linux find command is one of the most important and frequently used command-line utilities in Unix-like operating systems. The find command is used to
The post 35 Practical Examples of Linux Find Command first appeared on Tecmint: Linux Howtos, Tutorials & Guides.
The post How to Clone a Linux Server with Rsync first appeared on Tecmint: Linux Howtos, Tutorials & Guides .
Cloning is the meticulous process of creating an exact replica of a live Linux server by employing the powerful rsync command-line tool, which is an
The post How to Clone a Linux Server with Rsync first appeared on Tecmint: Linux Howtos, Tutorials & Guides.

The post 16 Rsync Command Examples for Efficient File Synchronization first appeared on Tecmint: Linux Howtos, Tutorials & Guides .
Rsync (Remote Sync) is the most commonly used command for copying and synchronizing files and directories remotely as well as locally in Linux/Unix systems. With
The post 16 Rsync Command Examples for Efficient File Synchronization first appeared on Tecmint: Linux Howtos, Tutorials & Guides.
The post Programmer vs System Administrator: Which Career Path is Right for You first appeared on Tecmint: Linux Howtos, Tutorials & Guides .
Careers in the technology space and broad and diverse and require different sets of skills. Programming and Systems Administration are two occupations that stand out
The post Programmer vs System Administrator: Which Career Path is Right for You first appeared on Tecmint: Linux Howtos, Tutorials & Guides.
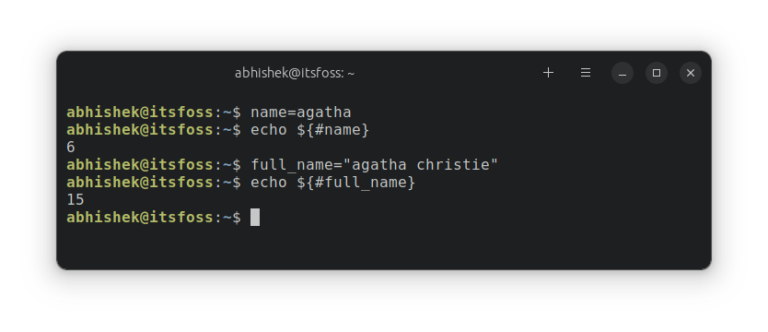
In this chapter of the Bash Basics series, learn to perform various common string operations like extracting, replacing and deleting substrings.
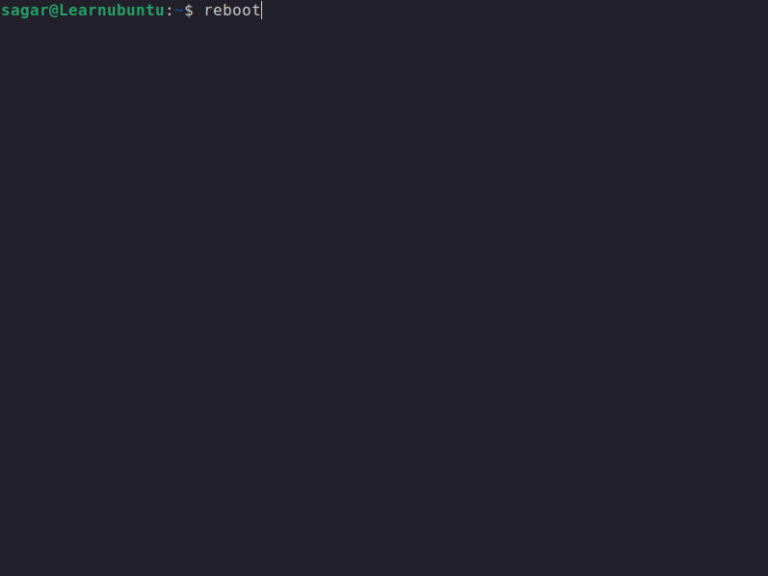
Need to access Grub while using Linux in a VM? Here’s how to do that.

The post How to Delete HUGE (100-200GB) Files in Linux first appeared on Tecmint: Linux Howtos, Tutorials & Guides .
In the realm of Linux terminal operations, a range of Linux commands are at our disposal for the purpose of effectively deleting or removing files.
The post How to Delete HUGE (100-200GB) Files in Linux first appeared on Tecmint: Linux Howtos, Tutorials & Guides.

Take a look at China’s first open source OS and learn about the origins of btrfs filesystem among other things in this newsletter.


In our previous article we have demonstrated a working prototype of Host Identity Based Virtual Private Service or HIP-VPLS. Back then we used the Mininet framework. Here we are going to demonstrate how to deploy this system on a real hardware. We are going to use NanoPi R2S as the platform for HIP-VPLS. Just a reminder. Virtual Private LAN Services (VPLS) provide means for building Layer 2 communication on top of an existing IP network. VPLS can be built using various approaches. However, when building a production-grade VPLS solution one needs to have a clear picture of how such aspects as security, mobility, and L2 issues will be solved.
Host Identity Protocol (HIP) was originally designed to split the dual role of the IP addresses. In other words, HIP is a Layer 3.5 solution that sits between the IP and transport layers. HIP uses hashes of public keys as identifiers. These identifiers, or Host Identity Tags (HITs), are exposed to the transport layer and never change (well, strictly speaking, they might change if the system administrator will decide to rotate the RSA or ECDSA key pairs for instance, but that will happen rarely). On the other hand, HIP uses routable IP addresses (these can be both IPv4 or IPv6) as locators and are used to deliver the HIP and IPSec packets between the end-points. Overall, to identify each other and exchange secret keys, HIP relies on a 4-way handshake (also known as HIP base exchange, or HIP BEX for short). During the BEX, peers negotiate a set of cryptographic algorithms to be used, identify each other (since HITs are permanent and are bound to public keys HIP can employ a simple firewall based on HITs to filter out untrusted connections), exchange the keys (HIP can use Diffie-Hellman and Elliptic Curve Diffie-Hellman algorithms), and even protect from Denial of Service attacks using computational puzzles (these are based on cryptographic hash functions and ability of peers to find collisions in hash functions; the complexity of a solution is regulated by a responder in HIP BEX). HIP also supports mobility and uses a separate handshake procedure during which the peer notifies its counterpart about the changes in the locator (read the IP address used for routing purposes).
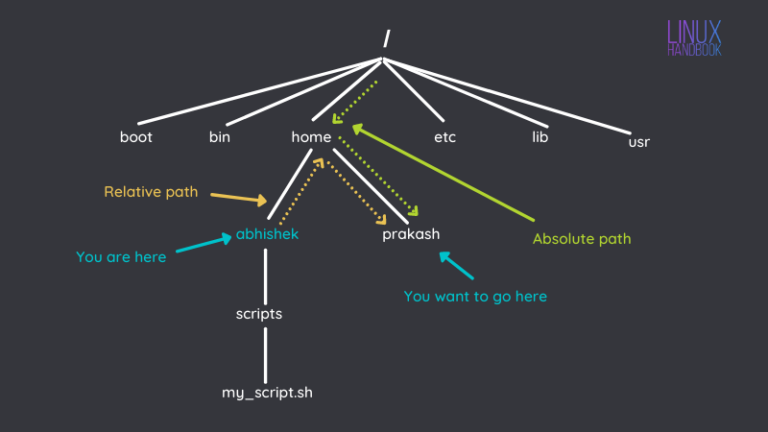
get familiar with the cp command for copying files and directories in the Linux command line.
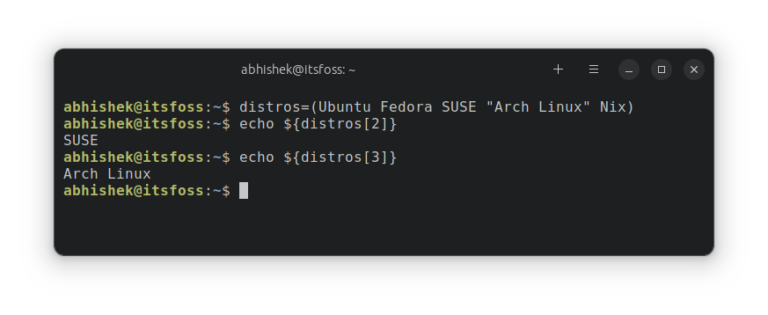
Time to use arrays in bash shell scripts in this chapter. Learn to add elements, delete them and get array length.
The post 8 Parted Commands to Manage Disk Partitions in Linux first appeared on Tecmint: Linux Howtos, Tutorials & Guides .
Parted is a renowned command-line utility designed to facilitate the management of hard disk partitions in a user-friendly manner. With Parted, you can effortlessly perform
The post 8 Parted Commands to Manage Disk Partitions in Linux first appeared on Tecmint: Linux Howtos, Tutorials & Guides.